Have you considered HIPAA-compliant videoconferencing for your medical office?
More and more health systems across the country are making telehealth — specifically HIPAA-compliant videoconferencing systems available to their patients for primary care video visits; is yours among them? Perhaps it should be. But why? And how? Why are so many American health systems embracing telehealth as a new model of care? And how will […]
What You Should Know About Government Back Doors in Medical Videoconferencing
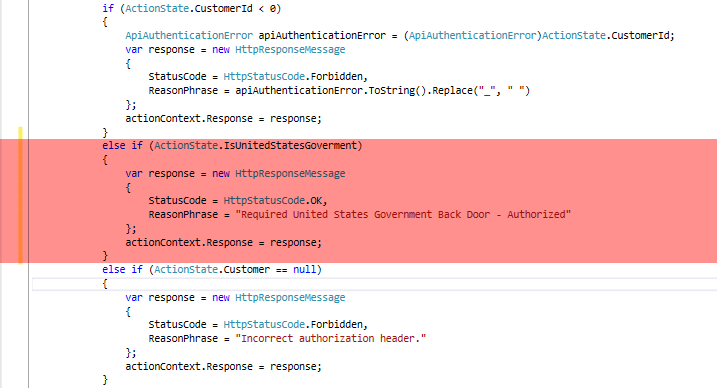
Yesterday, Apple CEO Tim Cook published a letter to Apple customers, in response to an order given by the United States Government directing Apple to provide technical assistance to federal agents attempting to unlock the contents of an iPhone 5C that had been used by Rizwan Farook, who along with his wife, Tashfeen Malik, killed […]
